Wigwam is a great alternative to your current crypto wallet
A solution that will satisfy all your needs
Download Extension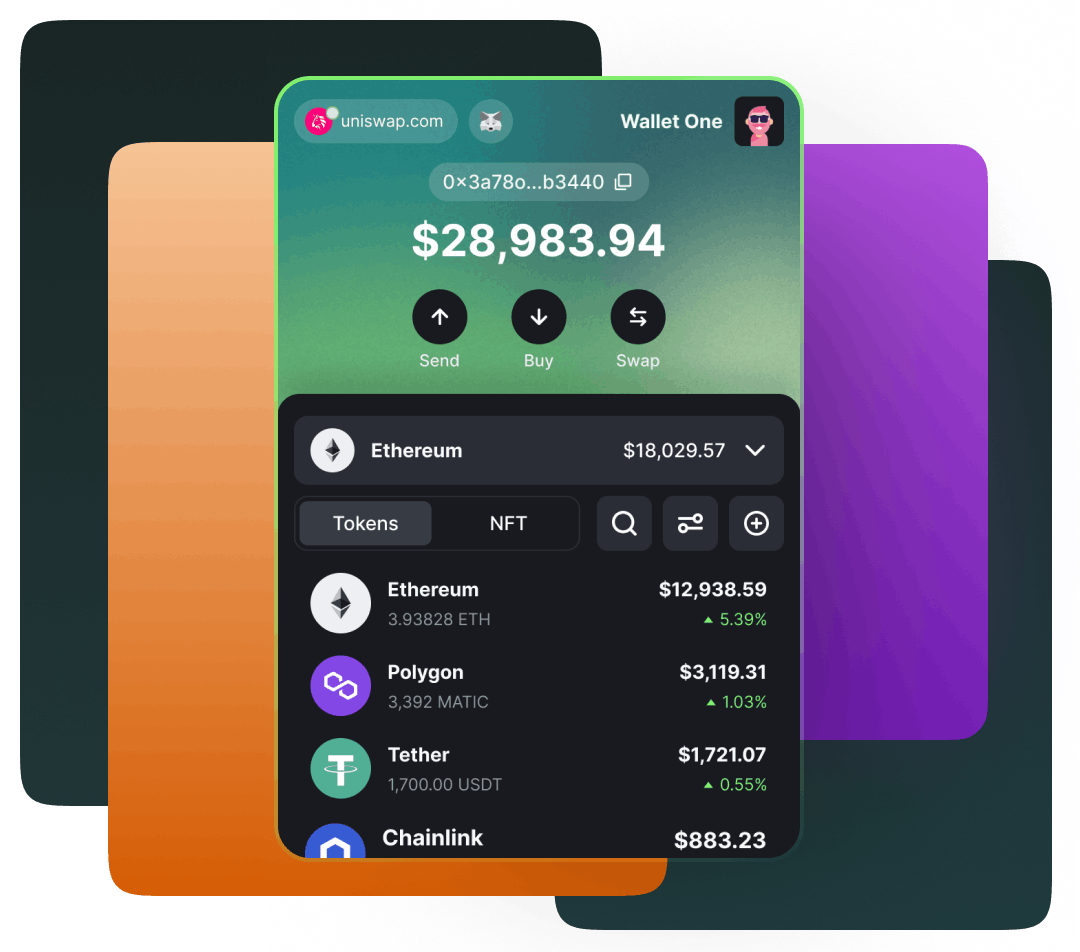
Why to choose the Wigwam wallet
Multiple blockchains
No fuss, no muss— Wigwam comes pre-loaded with multiple blockchains so you can dive right in

Buy crypto via Card
Use your card to effortlessly buy desired tokens in mere moments
Crypto exchange
Swap your tokens effortlessly with Wigwam's intuitive inbuilt exchange

Phishing protection
Unique icon generation for each wallet ensures you're always secure from phishing threats

NFT gallery
View and manage your digital collectibles in a convenient gallery

Support all token standards
Wigwam is a great wallet to hold your ERC-20, ERC-721 and ERC-1155 tokens

Portfolio tracking
Keep an eye on your portfolio with instant token value updates
Compare Wigwam Web 3 wallet with other popular crypto solutions
FAQ
- Custodial Wallets
These are wallets where a third party holds the private keys, typically a centralized exchange or service provider. While this can offer convenience, it also means that users don't have complete control over their assets, and the service provider can lock these funds.
- Self-Custodial Wallets (or Non-Custodial Wallets)
In these wallets, the user has full control over their private keys and, consequently, their funds. The responsibility of safeguarding the keys and wallet security lies entirely with the user and requires high responsibility for protecting their own funds.
- Hot Wallets
These are wallets that have access to the Internet. They are convenient for frequent transactions and are typically used for storing small amounts of crypto or work with DeFi services. Metamask is an excellent example of a hot wallet. However, being online, these wallets are more vulnerable to cyberattacks and hacks.
- Cold Wallets
These are offline wallets used to store large amounts of crypto over long periods securely. Since they are offline, they are immune to online hacks. Paper wallets and hardware wallets are examples of cold wallets.
- Seed Phrase: It's a series of words (usually 12 to 24) that is used to recover a crypto wallet. The seed phrase generates the private keys for the wallet. Keeping the seed phrase safe and confidential is crucial because anyone with access to it can access and control the funds in the wallet.
- Private key: is a cryptographic key unique to each wallet, allowing the owner to access and manage their funds. It's essential to keep the private key confidential. Someone else can control your assets if they gain access to your private key.
When choosing a blockchain wallet, consider the following factors:
- Security: Ensure the wallet follows the latest security updates, has passed security audits, and has earned market trust.
- Reputation: Check reviews and feedback from other users.
- User Interface: A user-friendly interface can make transactions and management more effortless.
- Compatibility: Ensure the wallet supports the cryptocurrencies you intend to use.
- Backup & Recovery: Look for wallets that offer backup and recovery options.
- Development & Support: A regularly updated wallet with active customer support is preferable.
A crypto wallet is a digital tool for storing, managing, and transacting cryptocurrencies. It consists of a public key, like an address that others can see and send funds to, and a private key, known only to the owner and used to sign transactions and access the funds. When someone sends you crypto, they transfer ownership of the coins to your wallet's address. To spend those coins, the private key stored in your wallet must match the public address to which the coins were sent. To conduct any transaction, a crypto wallet must have access to the blockchain. So, even cold wallets need access to the Internet to send tokens.
A hardware crypto wallet is a physical, electronic device designed to store cryptocurrencies' private keys securely. Since it's a form of cold storage (offline), it's immune to online hacks. Transactions are signed on the device and then broadcast to the blockchain, ensuring the private keys never expose themselves to internet-connected devices. Popular examples include Ledger Nano S and Trezor.